Android 4.0 Ice Cream Sandwich
Spy in the Watch

Specifications:
- Watch With A Micro Mini Video Spy Cam Built-in
- AVI Format (352×288) At 15fps
- Metal And Glass Construction
- Gear Driven Time in Hours, Minutes, Seconds
- Memory: 2GB
- Record Format: AVI (352×288), 15fps
- Built-in MIC
- Recommended Max Range for Objects: 2~3 Meters (Audio 1~2 Meters)
- Power Source: Built in Rechargeable Li-ion Battery (recharge directly from USB port)
- Analog 12 Hour Display (Hour, Minute, Second Hands)
- Metal And Glass Construction
- Back Clasp Design
- Time Adjustment Via Crown
- USB Port
- LCD Status Indicator
- Operating System Compatibility: Windows 98SE / ME/ 2000 / XP / Vista
- Dimension: Watch Face 50mm x 50mm x 15mm (L x W x D)
- Easy Recording Start And Stop
- Continuous Recording Until Memory Is Full Or Manual Shut Off
- Plug and Play (windows 2000 or later)
Digital Binoculars

The onboard memory is only 32MB but this can easily be expanded up to 2GB and the USB port makes it easy to get photos moved onto your computer.
Virtual Keyboard

USB Charagable AA Batteries


These standard AA batteries can be re-charged through any USB port. Each battery comes with a colorful green cap that pulls back to reveal a port, and then snapped back into place for use.
Wireless Charging

The Source will carry the latest electronics for the upcoming holiday season such as: a children's 12mp camera, a Bluetooth headset, DJ Hero and a wireless charging travel mat.
Future of Internet Search
After the launch iPad, Apple is looking forward to completely change the way people search. No more hassles of typing keywords, searching results. Apple is developing new device which is going to change the way you search. Google, Beware!! This device has a Touch screen, built in camera, scanner, Wi-Fi, Google maps and much more. Here are few pictures of the device and its uses. View a building through it, and it gives you all the information about that building. Choose a building and touch a floor and it tells you more details of the building. You can use it when you want to know a car model, an insect name, what kind of food is served at a restaurant and how much, who built a bridge, etc. etc.
Built in Scanner
Built in Dictionary:
Indoor Guide:
Automatic Simultaneous Translation:
Search Keyword:
Nutrition:
Search Beyond Time:
Power of Visualization:
Future Shopping:
Hybrid Dual Portable Computer

Mobile Intelligent Ubiquitous aka MIU has unveiled the third generation of its Hybrid Dual Portable Computer (HDPC). The new model offers a 4.1 inch TFT display (800 x480 resolution), a 2.4 inch AMOLED internal display (320 x 240 resolution), ARM processor for menial tasks, Intel Atom processor, Windows CE operating system and DMB navigation capability.
Wi-Fi Umbrella
 The high-tech brolly allows you to take pictures with a built-in camera. These can be uploaded to Flickr via a wireless internet connection and within two minutes you can watch downloaded photo-streams on your umbrella screen with a simple wrist-snapping movement.
The high-tech brolly allows you to take pictures with a built-in camera. These can be uploaded to Flickr via a wireless internet connection and within two minutes you can watch downloaded photo-streams on your umbrella screen with a simple wrist-snapping movement.Invented in Tokyo the Pileus umbrella also has GPS and a digital compass, which uses Google Earth to help you navigate yourself around the world. They are working on incorparating a video camera as well.
Six Point Charging Device

Introducing a six point charging device, which allows the user to charge up to six devices simultaneously.
Chargepod, which comes with many versions of power adapters, these are controlled by a system called voltage regulator technology, which will make sure that each device that is connected to it will only get the right amount of power, this is essential for the long life of the device. Where the wire is connected to the Chargepod there is a cool blue indicator light, which shows what device is on charge.
Steganography
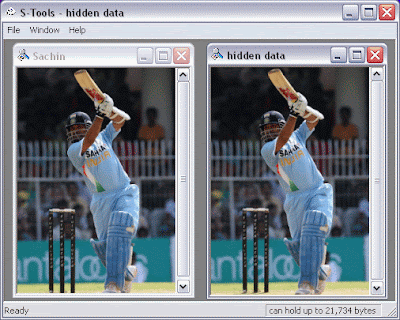
Steganography is the art of hiding the message in an image, audio or video file.




























